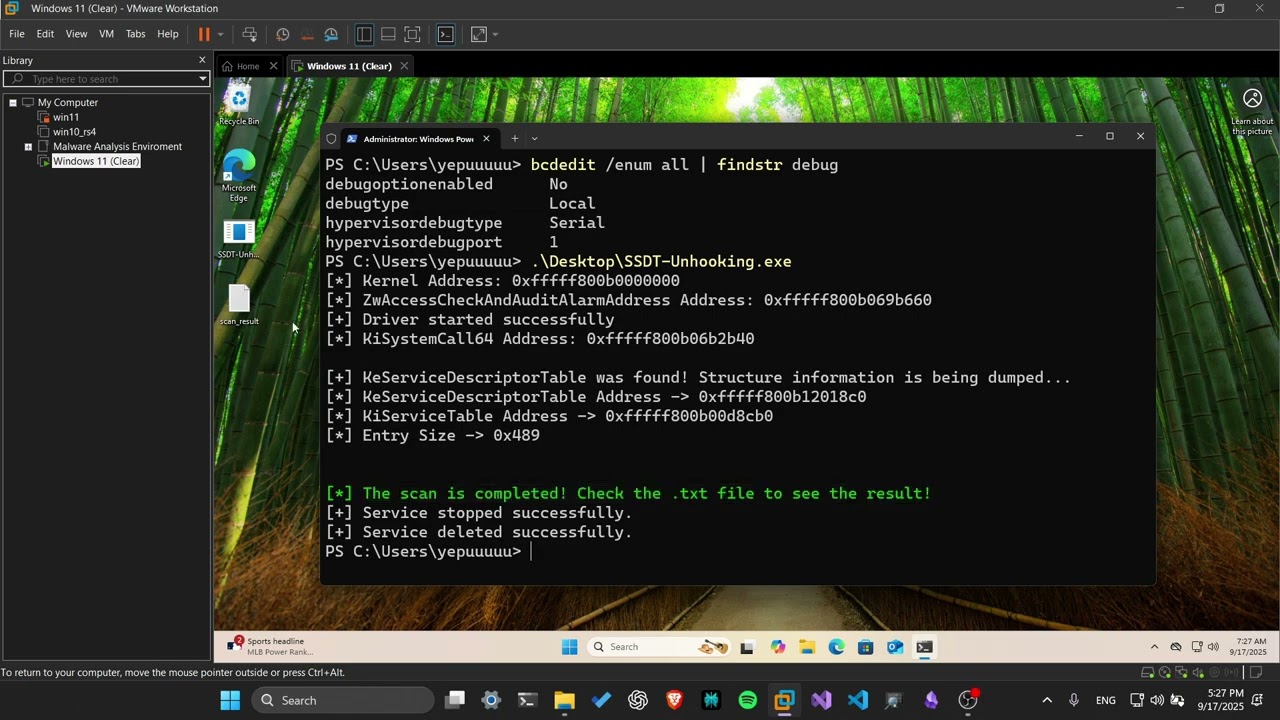
The project uses a vulnerable driver (RTCore64.sys) to read kernel memory and compare live SSDT function pointers and code bytes with their clean counterparts from ntoskrnl.exe.
Warning
This project is intended for educational and research purposes only. It interacts with low-level system components and uses a known vulnerable driver to access kernel memory. Do not use this project for malicious purposes, unauthorized penetration testing, or in production environments.
This project identifies modified SSDT entries by comparing the original bytes of kernel routines with those of the live system. Since direct user-mode access to kernel memory is restricted, the project employs a BYOVD (Bring Your Own Vulnerable Driver) approach with RTCore64.sys, enabling the safe reading of kernel memory in a controlled environment. First, the program reads the SSDT base and entry size, then calculates the address of each routine and retrieves the original opcodes from ntoskrnl.exe. It then compares these original bytes with the live kernel bytes and flags any differences as potential hooks. Rather than using hardcoded offsets, critical kernel functions, such as KiSystemCall64, are located dynamically.
All detected hooks are logged for further analysis, providing insight into how kernel routines may have been modified.
You can check out my blog for more details about the project.
Before the execution, you need to put the RTCORE64.sys file into \System32\drivers. The project will load and start this driver.